Best Practices for SAML Single Sign-On (SSO) in EA SaaS
The aim is to ensure an optimal experience for all EA SaaS users with minimal hassle. This article focuses on demonstrating how an admin can seamlessly manage users and their interactions within the EA model repository. By leveraging predefined groups in the EA model and simplified access control Profiles in the EA SaaS Portal, assigning varying Permissions and Restrictions to different user groups can be effortlessly achieved.
Prerequisite
- An Admin User Account has to log into the Prolaborate Portal.
- Create an Access Control Profile with a user group where SAML Single Sign-On (SSO) users can directly get assigned to those groups from the SAML groups.
What we cover below
- How to Create a User Group in Azure SAML and Prolaborate & EA Saas Portal to reuse the group for SAML configuration.
- How to set Permission and Restriction for SAML users in EA model.
- How to configure Access Control Profile for SAML users.
EA SaaS Flow

Create User Groups in Prolaborate Portal
Create a general group for each team.
To create a group, click on Menu > User Group Management.
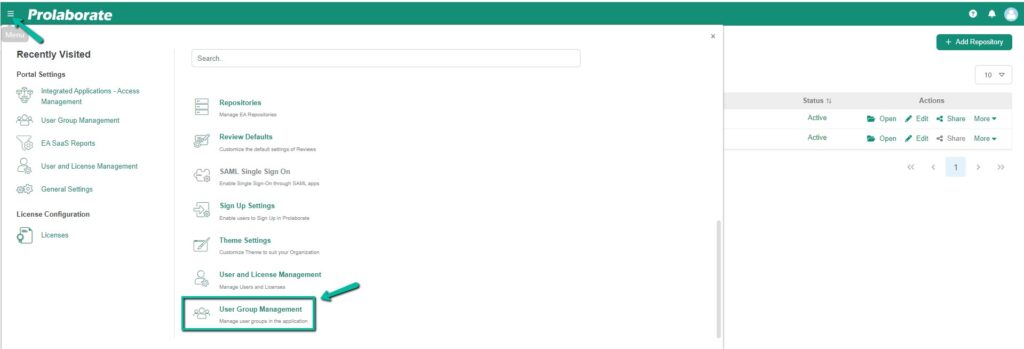
And “Click > Create User Group” as shown in the image below.
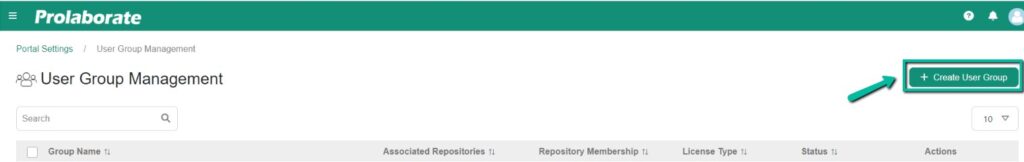
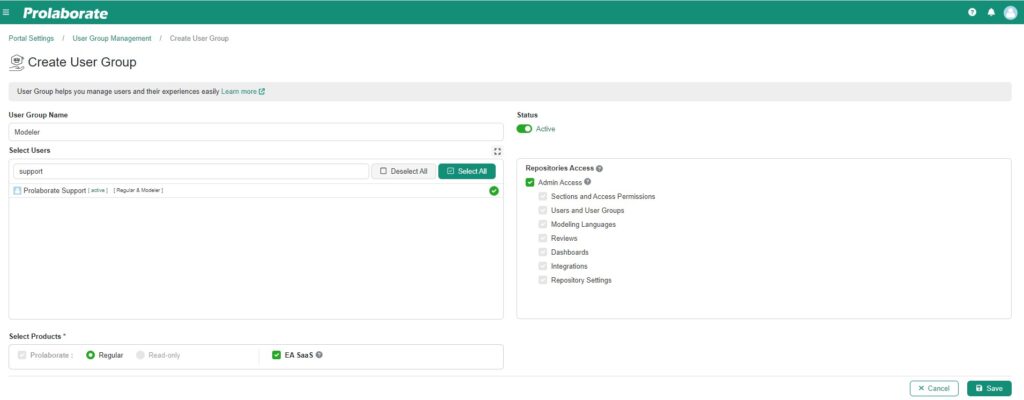
| Fields | Description |
|---|---|
| User Group Name | Enter the name of the user group. |
| Select Users | Assign the users to the respective group. |
| Repositories Access | Provide repository access based on your group |
| Select Products | Choose the specific products |
After entering the above details, click on “Save” to create the user group.
Access Control Profiles
When a SSO user logs in for the first time, they are automatically registered to Prolaborate & EA SaaS Portal. Configure the User groups in Access Control profiles by following these steps.
Click on Menu > Access Control Profile
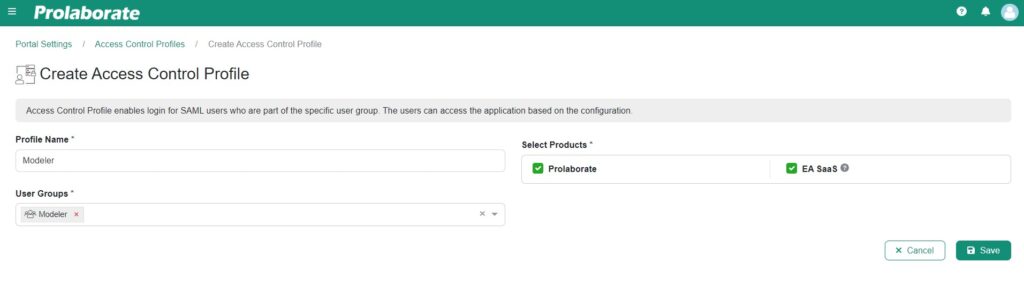
Click on Create Profile.

Name the profile and define the groups, then click the save icon to retain the Access Control Profile. For more information about Access Control Profiles, click here.
SAML Settings
1. Configure the Service Provider and Identity Provider Configuration on the SAML settings page. For more details on the SAML Single Sign-On Configuration, click on the link here.
2. Once the SAML group-based Restriction gets enabled, you can choose the Access Control profile that is created as mentioned above and fill in the Name of the SAML group name that was assigned in the SAML IDP portal as shown below.
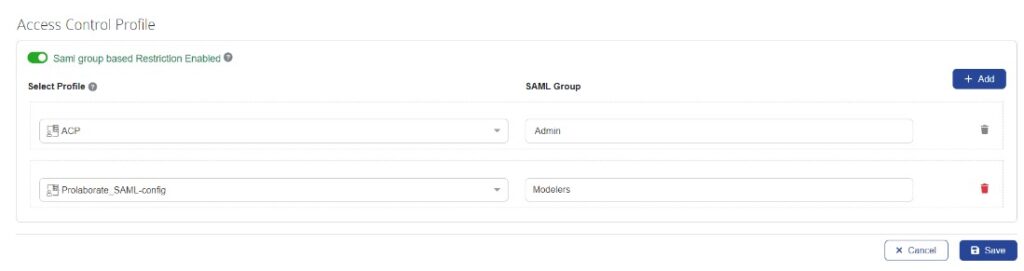
3. This configuration ensures that users belonging to the specified SAML group will be automatically granted access to Prolaborate and EA SaaS based on the Access profile you established in the SAML settings.
4. Click “Save” icon after the Configurations.
Setup Group in EA with Permissions and Restrictions on EA SaaS
Assign the right permissions to each group for each EA model repository.
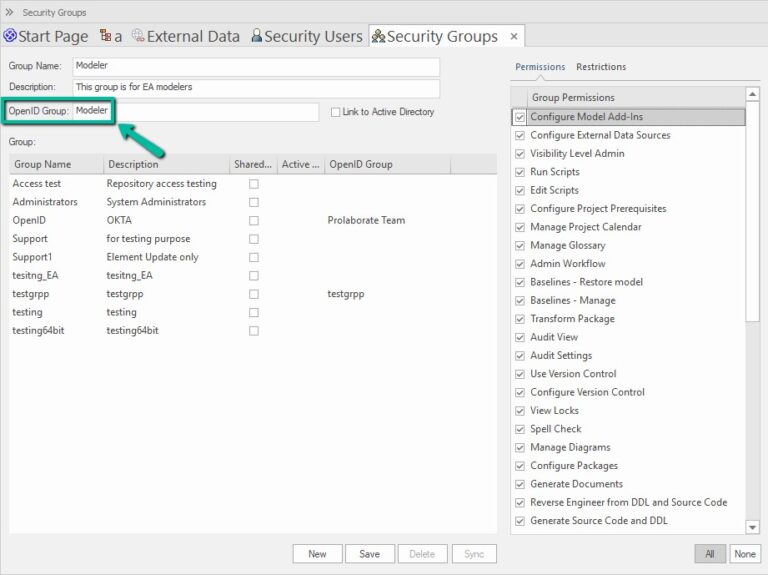
Note:
The value entered for ‘Open ID Group’ should be the same as the group name of the group created in the previous step in the EA SaaS Portal.
Click “Save” after the configuration.
Conclusion
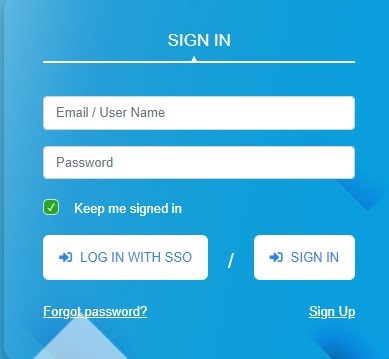
Once the configuration is done and SSO is enabled, users will start to see a new button on the authentication portal called ‘Login with SSO’ and they can click on it to login with their SSO credentials.
Upon selecting the SSO login option, the landing page will be displayed, featuring EA SaaS and Prolaborate, provided that the SSO user is assigned to both Prolaborate and EA SaaS.

Clicking ‘Open Project in Prolaborate’ will launch Prolaborate based on the access permissions configured for SSO, displaying the model according to the user’s access permissions.
Similarly, choosing “Open Repository in Sparx Enterprise Architect” will open Enterprise Architect with a Pinned model connection. By clicking on the model and selecting “OpenID login,” the model will be accessible based on the group restrictions assigned to the user.